https://www.webroot.com/us/en/home/products/wsa-installer-download
webroot introhttps://stasupteltd.sjv.io/c/6094923/2621608/29798
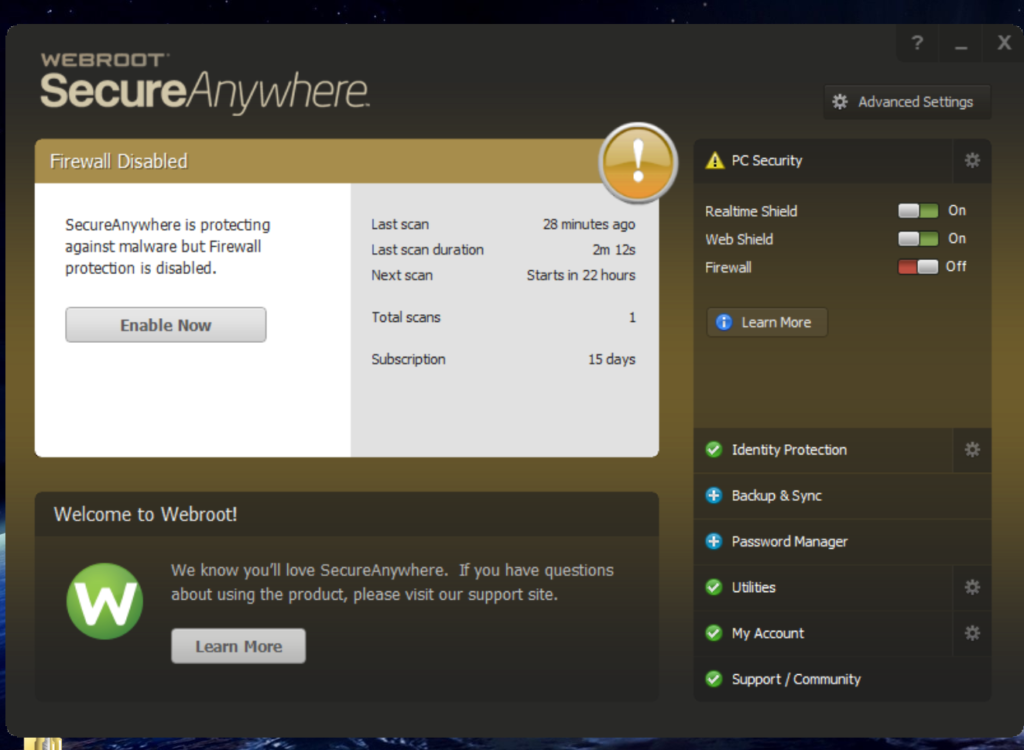
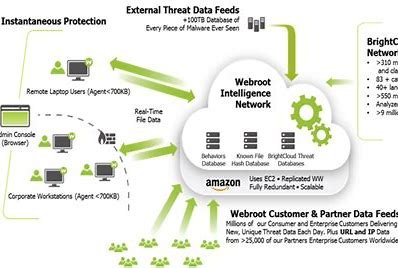
Webroot is a cybersecurity company that provides advanced threat protection and security solutions for individuals and businesses. Known primarily for its antivirus software, Webroot uses cloud-based technology to deliver real-time protection against a wide range of cyber threats, such as viruses, malware, ransomware, and phishing attacks.
One of Webroot’s key features is its lightweight, fast scanning engine, which does not slow down system performance. The company’s solutions are designed to offer protection across multiple devices, including computers, smartphones, and tablets. Webroot also focuses on providing tools for secure browsing, identity theft protection, and data privacy.
Some of Webroot’s main offerings include:
- Webroot SecureAnywhere Antivirus: Protects against malware, viruses, and other threats with minimal system impact.
- Webroot SecureAnywhere Internet Security Plus: Includes additional features such as identity theft protection and secure online banking.
- Webroot Business Solutions: Tailored solutions for businesses, providing enterprise-level security and management tools for IT administrators.
Webroot’s cloud-based approach enables continuous updates and improves detection capabilities without requiring significant resources from the user’s device.
get 40% off 3 months or a free trial webroot
features and functionality
When evaluating a product or service, features and functionality play a critical role in determining its overall usefulness and performance. The features should align with the needs of the user, providing a smooth and efficient experience. The functionality refers to how well these features work in practice and whether they contribute to the intended purpose without issues.
Key features typically include options like real-time scanning, customizable settings, and seamless integration with other tools or devices. The functionality aspect focuses on how effectively these features are implemented, ensuring the product is both intuitive and easy to navigate.
Common Features to Expect
- Real-Time Protection: Continuous scanning to detect threats as they arise, providing a proactive defense against malware, viruses, and other harmful software.
- Customizable Settings: Ability to adjust various settings such as scan schedules, notifications, and specific protections according to user preferences.
- Automatic Updates: The product should automatically update its database and software to keep up with emerging threats and vulnerabilities.
- Cloud-Based Features: Some advanced systems incorporate cloud storage to enhance data backup and real-time threat detection.
- User-Friendly Interface: A clean, intuitive design that allows users to easily access and use all features without confusion.
Functionality in Action
The functionality of these features ensures that they operate efficiently without causing significant system slowdowns or compatibility issues. A well-designed product will work in the background without interrupting the user’s experience, all while offering strong protection and ease of access to features.
For example, real-time protection should not only scan for threats but do so without consuming excessive resources or slowing down the device. Additionally, any notifications or alerts should be clear and actionable, helping users address issues promptly without causing frustration.
https://tayo99.com/2025/01/10/constant-contact-review-2025best-email-marketing-tool/
Ease of Use
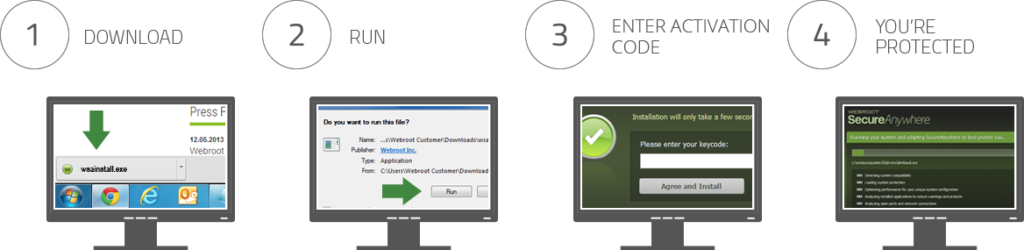
When assessing any product or service, ease of use is one of the most important factors to consider. A product with great features and functionality might fall short if it’s complicated to navigate or difficult to understand. The ease of use directly impacts the overall user experience and determines how quickly users can set up, use, and benefit from the product.
A product that is easy to use will feature a straightforward interface, minimal setup steps, and clear instructions, making it accessible to both beginners and experienced users. The goal is to ensure that users can make the most of the product’s features without getting bogged down by unnecessary complexity.
Key Aspects of Ease of Use
- Simple Installation Process: The installation process should be quick and easy, with minimal steps. Ideally, it should involve no more than a few clicks or taps, and it should guide users through each step.
- Intuitive Interface: The interface should be simple and self-explanatory, with easily identifiable icons and navigation. Important functions should be easy to access, and settings should be clearly labeled.
- Clear Instructions and Onboarding: When users first launch the product, a brief tutorial or setup guide can be incredibly helpful. A clear introduction to the main features and functionalities helps users get started quickly.
- Minimal Configuration: A product that is easy to use often requires minimal customization. The default settings should work for the majority of users, but the ability to adjust settings easily is still important for those who want more control.
- Accessible Support: If users encounter issues, easy access to help resources—like a support page, live chat, or FAQ—can make a big difference. The faster a user can resolve any problems, the smoother their experience will be.
Why Ease of Use Matters
Ease of use ensures that users can fully benefit from a product without unnecessary frustration. When a product is user-friendly, it reduces the learning curve and encourages users to engage with the product more frequently. Whether it’s a first-time user or someone with more experience, the simplicity of use improves satisfaction and overall efficiency.
Performance and Speed
When choosing any product or service, performance and speed are crucial factors that cannot be overlooked. A product that delivers high performance and fast operation will ensure users can complete tasks efficiently without delays. In contrast, slow performance or lag can significantly reduce user satisfaction and productivity.
Performance refers to how well the product operates, including its ability to handle tasks without crashing or freezing. Speed, on the other hand, relates to how quickly the product executes actions and responds to commands. Together, these two factors are essential for a seamless user experience.
Key Aspects of Performance and Speed
- Fast Execution: A high-performing product will execute tasks quickly and efficiently, such as scanning for threats, loading pages, or processing data. It should be responsive, ensuring minimal wait times.
- Low Latency: For products requiring real-time interaction, like security software or gaming applications, low latency is vital. Users should experience no noticeable delays between performing an action and receiving feedback.
- Resource Efficiency: A product that performs well will not consume excessive system resources (such as CPU or memory). It should work smoothly in the background without causing slowdowns on other tasks or applications.
- Quick Start-Up Time: The time it takes for the product to launch or start up is also important. A quick start-up means users can begin using the product without waiting, enhancing convenience.
- Handling Large Files or Tasks: High-performance products can handle large files, extensive processes, or complex tasks without lag or crashing. This is especially important for data-intensive tools or applications that users rely on for more demanding work.
Why Performance and Speed Matter
The performance and speed of a product directly impact how users interact with it on a day-to-day basis. Slow or underperforming products can lead to frustration and may cause users to seek out alternatives. A fast and efficient product, on the other hand, increases user productivity, satisfaction, and retention.
In areas like security software, performance is especially critical. A slow security scan or delayed malware removal could leave a device vulnerable for longer than necessary. In contrast, a quick and efficient security tool can offer peace of mind and allow users to focus on other tasks without interruption
Security and Threat Detection
Security and threat detection are at the core of many modern software products, especially those designed to protect your data and devices. The primary function of security tools is to safeguard against malicious attacks, while effective threat detection ensures that potential risks are identified and addressed before they cause harm.
In today’s digital world, where cyber threats are ever-evolving, having strong security and threat detection features is essential for maintaining the safety of personal information, sensitive data, and system integrity.
Key Features of Security and Threat Detection
- Real-Time Protection: The ability to detect and neutralize threats as soon as they appear is crucial. Real-time protection actively monitors for suspicious activity, ensuring that viruses, malware, or ransomware do not infect your system.
- Virus and Malware Scanning: Comprehensive scanning that checks files, emails, downloads, and websites for known and unknown malware threats. Scanning should be fast, efficient, and regularly updated to recognize new threats.
- Heuristic Analysis: This feature analyzes files based on their behavior, rather than just known signatures, to detect unfamiliar or new threats that might not yet be included in traditional virus definitions.
- Behavioral Detection: Monitors how programs behave during operation, looking for unusual actions that might indicate malware or a breach. This helps in catching threats that might otherwise go undetected by signature-based methods.
- Firewall Protection: An active firewall helps block unauthorized access to your system while allowing legitimate traffic. This additional layer of security helps prevent attacks like hacking or unauthorized data transfers.
- Phishing Protection: Protects users from phishing attempts that try to steal personal information, credentials, or financial data by impersonating legitimate entities through fake emails or websites.
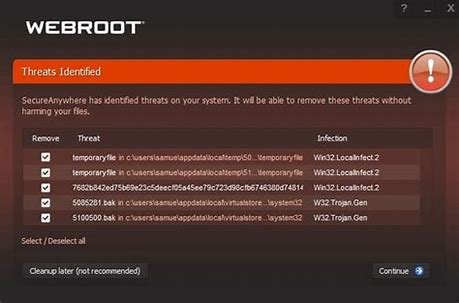
- Quarantine and Removal: Threat detection systems should have a quarantine feature that isolates suspicious files and provides users the option to either delete or restore them, based on further analysis.
Why Security and Threat Detection Matter
Security and threat detection are essential in today’s interconnected world. Cyber threats are growing in sophistication, and without robust detection mechanisms, users are vulnerable to everything from identity theft to data breaches and system failures.
A well-designed threat detection system works proactively to identify risks, alert users to potential dangers, and neutralize threats before they can cause damage. The ability to stay ahead of emerging threats ensures a safer digital environment and fosters confidence in the security product being used.
Effective security and threat detection also means lower chances of experiencing downtime, financial losses, or the long-term effects of a security breach. As cybercriminals continually develop new tactics, threat detection tools need to be adaptive and frequently updated to remain effective.
Pricing and Plans
When evaluating any product or service, understanding the pricing and plans is essential for determining its value. Pricing structures can vary widely depending on the features offered, the level of support, and the type of service. A clear breakdown of pricing and plans helps users choose the best option for their needs and budget.
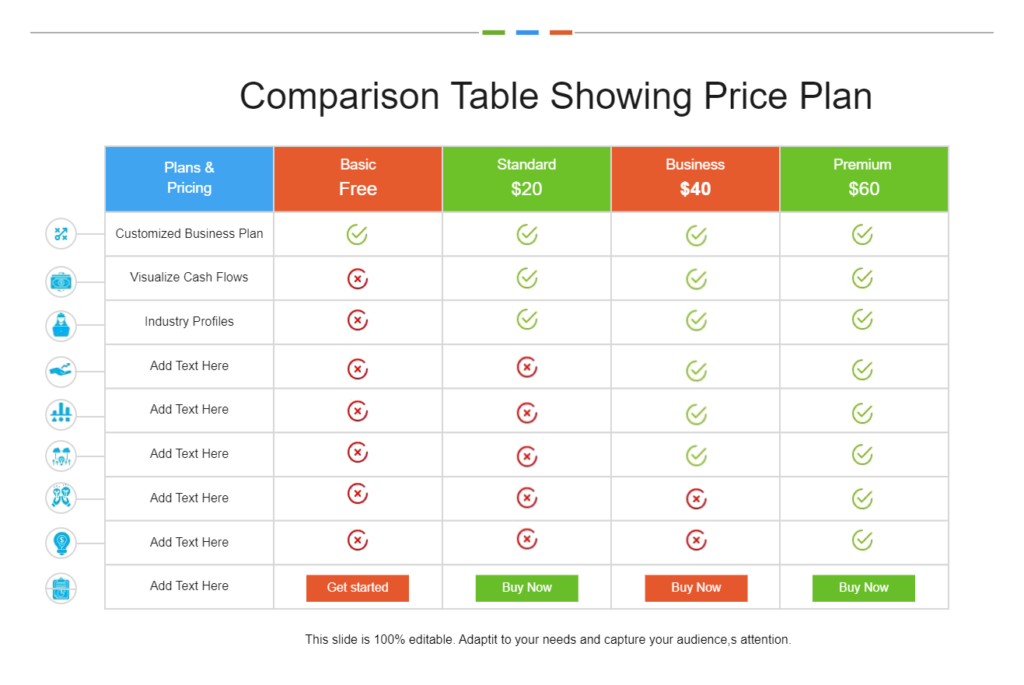
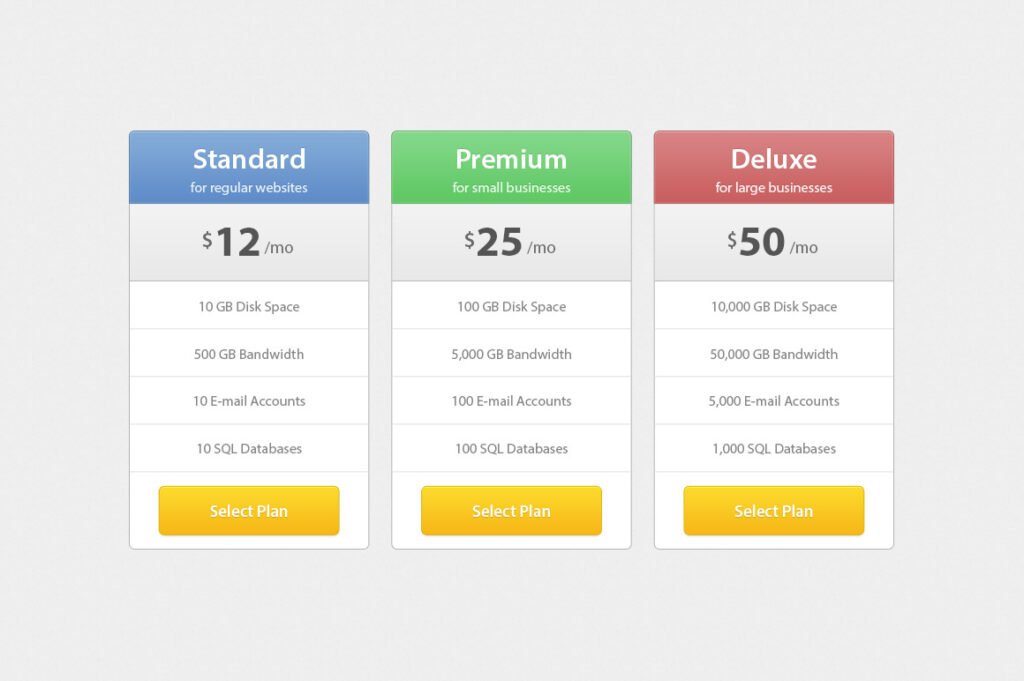
For most software or subscription-based services, pricing is typically divided into multiple tiers, each offering different features or levels of access. These plans may cater to individual users, small businesses, or larger organizations, providing flexibility to suit various needs.
Key Aspects of Pricing and Plans
- Subscription Tiers: Many products offer multiple subscription levels, such as basic, premium, or enterprise. Each tier generally provides additional features or more extensive usage options. The pricing for these tiers should reflect the value and additional benefits they offer.
- Free Trials or Freemium Models: Some services provide a free trial period or a freemium version that gives users access to a limited set of features. This allows users to try the product before committing to a paid plan, ensuring it meets their needs.
- One-Time Payment vs. Subscription: Some products may offer a one-time payment option for lifetime access, while others operate on a recurring subscription model (monthly or yearly). The subscription model may be more flexible, offering updates and ongoing support as part of the plan.
- Discounts and Promotions: Many companies offer discounts for long-term commitments (such as annual subscriptions) or promotional prices for new users. It’s essential to check for any special deals or seasonal offers that may make the product more affordable.
- Money-Back Guarantee: A solid money-back guarantee can provide users with added confidence when purchasing. This allows them to try the product risk-free, knowing they can get a refund if it doesn’t meet expectations.
- Add-Ons and Upgrades: In some cases, products may offer add-ons, such as extra storage, advanced features, or additional user licenses. These should be clearly outlined as optional upgrades to the base plan.
Why Pricing and Plans Matter
Understanding pricing and plans is crucial for users to determine whether the product fits within their budget and if the value matches the cost. Transparent pricing can also help avoid confusion or hidden fees later on. Additionally, having clear tiered options allows users to select the plan that best fits their needs without overpaying for unnecessary features.
For example, if a user only needs basic functionality, a lower-tier plan might be sufficient. However, for those who require advanced features or business-grade services, upgrading to a premium plan might be more suitable. Pricing transparency ensures that users feel confident in their purchase and can easily compare different plans.
https://stasupteltd.sjv.io/c/6094923/2621608/29798
Customer Support and Help Resources
Customer support and help resources are critical components of any product or service, ensuring that users can quickly resolve issues and get the most out of their purchase. The availability and quality of support can significantly impact user satisfaction, especially when troubleshooting technical problems or learning how to use a product effectively.
A robust support system provides users with multiple channels to seek assistance, from self-help resources to direct communication with support teams. Efficient and accessible customer support and help resources can make the difference between a frustrating experience and a smooth, problem-free one.
Key Aspects of Customer Support and Help Resources
- 24/7 Support Availability: Round-the-clock support ensures that users can reach out for assistance at any time, no matter where they are located. Whether it’s through live chat, phone support, or email, having support available at all hours is a valuable feature.
- Multiple Support Channels: The best customer support systems offer several communication channels, including live chat, phone support, email, and even social media. This flexibility allows users to choose the most convenient option for their needs.
- Help Center and Knowledge Base: A well-organized help center or knowledge base with articles, tutorials, and FAQs is an essential resource. These self-help options empower users to find solutions to common issues without needing to contact support.
- Community Forums: Many services provide community forums where users can ask questions, share tips, and discuss issues with other users. This peer-to-peer support can be especially helpful for troubleshooting or learning new ways to use the product.
- Ticketing System: A ticketing system allows users to submit detailed queries or issues, which are then addressed by support staff in a structured manner. This system helps ensure that complex issues are tracked and resolved promptly.
- Live Chat Support: Live chat is often one of the quickest ways to get help. It allows users to communicate with support agents in real time, often resolving issues faster than through email or ticketing systems.
- Video Tutorials and Webinars: For users who prefer visual learning, video tutorials and live webinars are great resources. These provide step-by-step guides for common tasks, troubleshooting, or advanced features.
Why Customer Support and Help Resources Matter
Having reliable customer support and help resources is vital because it helps users navigate challenges and get back on track quickly. When a problem arises, whether it’s technical or related to using a feature, timely assistance can prevent frustration and ensure users continue to have a positive experience with the product.
Well-established support systems also enhance user retention, as users are more likely to remain loyal to a product when they feel confident that help is easily accessible. Additionally, comprehensive self-help resources reduce the need for users to contact support, saving time for both the users and the support team.

Help Center
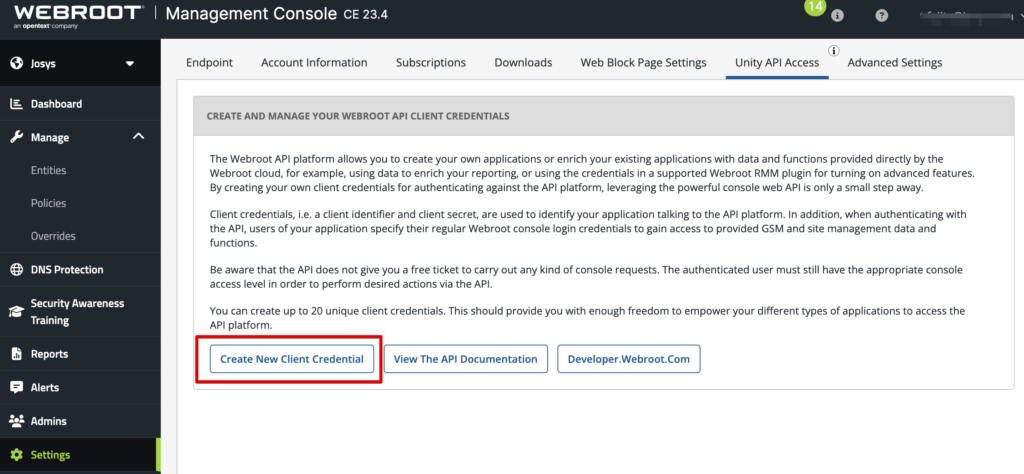
System Resource Usage
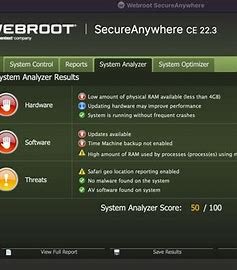
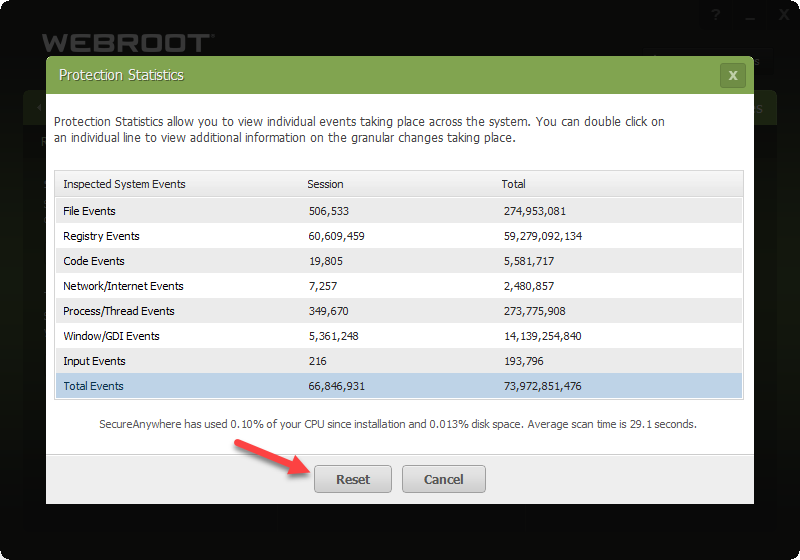
System resource usage refers to how much of your device’s resources—such as CPU, memory (RAM), disk space, and network bandwidth—are consumed by a product or service while it’s running. When evaluating software, it’s crucial to consider how efficiently it uses system resources, as excessive usage can lead to slower performance, system instability, and a poor user experience.
Efficient system resource usage ensures that a product operates smoothly without consuming too many resources, allowing users to multitask and run other applications without experiencing noticeable slowdowns. A well-optimized product should work in the background without causing noticeable impacts on other processes.
Key Aspects of System Resource Usage
- CPU Usage: High CPU usage can significantly slow down a device, especially when running multiple applications. A product that uses excessive CPU power will make the system feel sluggish, and may also cause overheating or battery drain on portable devices.
- Memory (RAM) Consumption: Efficient software uses minimal RAM, which helps keep your system running smoothly, especially if you have multiple programs open at once. Products that use too much memory can lead to lag, crashes, or even system freezes.
- Disk Space: Software should not take up excessive disk space, particularly if it’s a lightweight application. Large software packages or products that continually add files to your system can fill up storage, slowing down performance and affecting your device’s ability to store important data.
- Network Usage: For online applications, excessive network bandwidth usage can lead to slow internet speeds. If the product frequently uses large amounts of data, it could interfere with other online tasks, such as browsing, streaming, or video conferencing.
- Background Processes: Some software runs multiple background processes that can impact system performance. It’s important to check whether the software actively uses system resources when you’re not directly using it, such as during idle periods or updates.
Why System Resource Usage Matters
System resource usage is critical because if software consumes too many resources, it can cause your device to slow down, which in turn disrupts your workflow and can lead to a frustrating experience. This is especially true for users with older hardware or devices with limited resources.
Efficient resource usage ensures that the product can operate without significantly affecting the system’s overall performance. In contrast, software that is poorly optimized can lead to increased load times, system crashes, or a sluggish experience. For users who need to run several applications simultaneously, choosing software with light system resource usage is key to maintaining productivity.
A product that optimizes its system resource usage also helps extend the life of your hardware, reducing wear and tear on components like the CPU, memory, and hard drive. It also helps conserve battery life on portable devices like laptops and smartphones, making the product more portable and efficient.
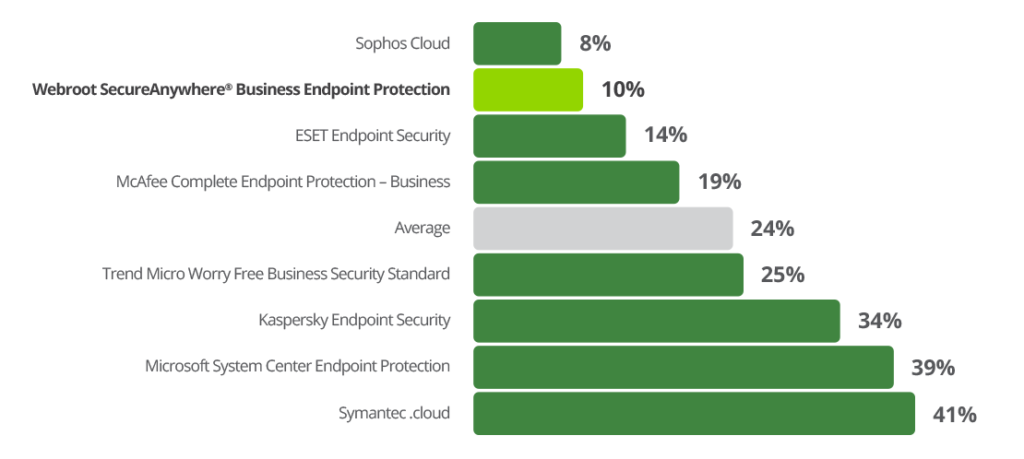
- Performance Benchmark Comparison
Detection Rates and Malware Removal
Detection rates and malware removal are two of the most important aspects to consider when evaluating security software. The effectiveness of a security product is largely determined by how accurately it detects threats and how efficiently it can remove them. High detection rates mean that the software is good at identifying potential security risks, while effective malware removal ensures that these threats are completely eliminated from your system.
When choosing a security solution, it’s vital to understand both the detection rate and how well the software can clean or quarantine detected malware to ensure your device remains safe from infection.
Key Aspects of Detection Rates and Malware Removal
- Detection Rate: This refers to the software’s ability to identify and flag threats, including viruses, malware, spyware, and ransomware. A high detection rate means the product can spot a wide range of known and emerging threats, even those that aren’t yet included in traditional signature databases. Top-rated products have detection rates of 99% or higher, ensuring that your system is protected against the majority of threats.
- Real-Time Threat Detection: Real-time detection continuously monitors your system for potential risks, scanning files, programs, and websites for malicious activity as you interact with them. The higher the detection rate, the less likely harmful malware will slip through unnoticed.
- Heuristic and Behavior-Based Detection: In addition to traditional signature-based detection, many modern security tools employ heuristic or behavior-based detection. These methods analyze the behavior of files and programs, looking for suspicious actions or code patterns that indicate potential threats, even if the threat is not yet recognized by signature databases.
- Malware Removal Process: Once malware is detected, the product should be able to safely remove it without causing damage to your files or system. A good malware removal tool will either quarantine or delete malicious files, ensuring that your system is fully cleaned and that no remnants of the malware remain.
- Rootkit and Advanced Malware Removal: Rootkits and other advanced malware types can be particularly challenging to detect and remove. High-quality security software includes specialized tools to root out these deeply embedded threats and completely clean your system.
- Quarantine and Recovery Options: When malware is detected, the best security software should offer quarantine features, isolating the infected files so they don’t spread. Users should also have options for restoring important files from backup in the event of a false positive or system disruption.
Why Detection Rates and Malware Removal Matter
The effectiveness of detection rates and malware removal is essential because malware can cause significant harm, from data theft and privacy breaches to system damage and financial loss. A high detection rate reduces the chances of a threat entering your system, while efficient malware removal ensures that any detected threats are eliminated before they can do harm.
Security software with high detection rates minimizes the risk of missing threats, while effective malware removal ensures that the product can restore your system to its original state without causing further issues. Both features work together to maintain the integrity of your system, providing peace of mind that your device is safe from a wide range of potential threats.
Additionally, as malware and cyber threats become more sophisticated, it is important for detection rates to be constantly updated and for malware removal tools to be capable of handling the latest threats. Security software that stays up-to-date and continuously improves its detection and removal capabilities is crucial for staying protected.
Additional Features (VPN, Password Manager, etc.)
When evaluating security software, it’s important to consider not only its core functionality, such as malware detection and removal, but also its additional features. These added tools can greatly enhance the user experience by providing extra layers of protection and convenience. Features like a VPN (Virtual Private Network), password manager, and others contribute to your overall online security, privacy, and efficiency.
Key Additional Features
- VPN (Virtual Private Network): A VPN is one of the most valuable additional features in security software. It encrypts your internet connection, ensuring that your online activity remains private and secure. Whether you’re browsing on public Wi-Fi or simply want to protect your data from prying eyes, a VPN creates a secure tunnel for your information, protecting it from hackers, ISPs, or even government surveillance.
- Benefits of VPN:
- Protects sensitive data when using public Wi-Fi.
- Hides your IP address, offering anonymity online.
- Allows access to geo-restricted content by changing your virtual location.
- Benefits of VPN:
- Password Manager: A password manager securely stores and manages your passwords, making it easier to use strong, unique passwords for every account. This feature automatically generates complex passwords and fills them in for you, reducing the risk of using weak or repeated passwords across multiple sites.
- Benefits of Password Manager:
- Eliminates the need to remember dozens of passwords.
- Ensures strong, unique passwords for each online account.
- Offers safe storage for sensitive information like credit card details.
- Benefits of Password Manager:
- Firewall Protection: A built-in firewall adds an extra layer of defense by monitoring and controlling incoming and outgoing network traffic. It prevents unauthorized access to your system and ensures that malicious software or hackers are blocked from exploiting vulnerabilities in your system.
- Antiphishing Protection: Antiphishing tools prevent you from falling victim to fraudulent websites or emails designed to steal your personal information. These tools work by detecting phishing attempts and alerting you to suspicious content before you can interact with it.
- Cloud Backup: Some security software includes cloud backup services that automatically back up your important files to a secure cloud storage. This ensures that your data is protected from hardware failure, ransomware, or accidental deletion, and can be easily restored if needed.
- Parental Controls: Parental controls help monitor and limit what children can access online. These features allow parents to block inappropriate content, monitor screen time, and set usage limits to ensure a safe and balanced online experience for younger users.
Why Additional Features Matter
Additional features like a VPN, password manager, and other security tools provide comprehensive protection and enhance your overall digital experience. While basic antivirus or antimalware features keep your system safe from common threats, these additional features focus on privacy, convenience, and online safety, offering protection in multiple areas of your digital life.
For example, a VPN protects your browsing activities and ensures anonymity, while a password manager helps you avoid common pitfalls like weak passwords and data breaches. Together, these features create a more secure and streamlined online experience, reducing the risk of personal data theft, fraud, or identity theft.
For users looking for all-in-one security solutions, these additional features can eliminate the need for separate, standalone apps, simplifying the user experience and saving time and resources. Whether you’re concerned about privacy, convenience, or peace of mind, these extra tools can address specific needs that go beyond basic malware protection.
- VPN Protection Diagram

User Reviews and Ratings
User reviews and ratings play a crucial role in helping potential buyers assess the effectiveness and reliability of a product or service. These reviews provide insights from real customers who have hands-on experience with the software, making them a valuable resource when making purchasing decisions. By looking at the overall ratings and reading specific feedback, users can better understand what to expect from a product, both in terms of its performance and user satisfaction.
Key Aspects of User Reviews and Ratings
- Overall Rating: The overall rating is often the first thing a user sees when browsing reviews. It typically ranges from 1 to 5 stars (or a similar scale), giving a quick snapshot of the general satisfaction level of users. A high rating generally indicates that the product delivers on its promises, while a low rating may signal issues that need further consideration.
- Pros and Cons: Many users highlight specific pros and cons in their reviews, helping potential buyers understand what the product does well and where it might fall short. For example, users may praise the software’s fast scanning speed but mention that it uses significant system resources. These detailed insights can help set realistic expectations.
- Feature Feedback: Reviews often discuss specific features of the software, such as ease of use, customer support, or additional tools like a VPN or password manager. This feedback is helpful for identifying which features are most valued by users and whether they live up to expectations.
- Support and Customer Service: Reviews frequently mention the quality of customer support and help resources. Positive feedback about quick, helpful support can reassure potential users, while complaints about poor service or slow response times could raise red flags.
- User Experience: Real-life experiences shared by users give a sense of how easy or difficult the software is to use. Whether it’s navigating the interface, setting up the software, or troubleshooting problems, reviews help potential buyers gauge whether the product is user-friendly and intuitive.
- Updates and Performance: Many users comment on how well the software performs over time, including any updates or patches released. If a product regularly improves its performance and security features, it’s likely to receive positive feedback, while a lack of updates or issues with stability might result in negative reviews.
Why User Reviews and Ratings Matter
User reviews and ratings are one of the most effective ways to gauge the true value of a product or service. They offer an honest look at a product’s real-world performance, going beyond the marketing and promises made by the company. Reviews also allow users to see how the product compares to alternatives in terms of features, performance, and customer satisfaction.
For example, a product with a high rating and positive reviews may be a good choice, but if users consistently mention issues with speed or functionality, it might be worth looking into alternatives. Similarly, negative reviews could help identify recurring problems, such as bugs or poor customer support, which may not be evident in official documentation or marketing materials.
Moreover, user reviews and ratings offer transparency, giving you the ability to make an informed decision before making a purchase. They help uncover both strengths and weaknesses, allowing you to weigh the pros and cons carefully.
- Rating Breakdown: A graphic showing a breakdown of the product’s ratings, such as the percentage of 5-star, 4-star, and lower ratings, can provide a clear visual of the overall user sentiment.
- Positive and Negative Review Highlights: Including snippets of both positive and negative reviews, with a focus on common themes, can give a balanced perspective of what users like and dislike about the product. Highlighting specific comments can make the content more engaging.
- Review Platform Screenshots: A screenshot of a review page from a popular platform (such as Google Reviews, Trustpilot, or the software’s official site) can give users a visual of where and how reviews are posted, adding authenticity and trustworthiness to the content.
- Customer Support Interaction Example: A visual of a positive customer support interaction, such as a chat window or email exchange, can demonstrate how the company addresses customer concerns and issues effectively.
Free Trials and Money-Back Guarantee
Free trials and money-back guarantees are important features that offer users a risk-free way to evaluate a product or service before making a long-term commitment. These options give you the opportunity to test the software’s performance, features, and compatibility with your system, while ensuring that you won’t be stuck with a product that doesn’t meet your needs.
Key Aspects of Free Trials and Money-Back Guarantee
- Free Trials: A free trial allows you to use the product for a limited time—usually ranging from 7 to 30 days—without paying. This period lets you experience the software’s core features and evaluate its functionality, speed, and ease of use. Some free trials offer full access to all features, while others may have restrictions or limitations on advanced tools.
- Benefits of Free Trials:
- Risk-Free Testing: You can explore the product’s features and interface without financial commitment.
- Performance Evaluation: Use the software in real-world conditions to assess how it performs on your system.
- Full Feature Access: Many free trials offer unrestricted access to the full version of the software, letting you test all functionalities.
- Limitations of Free Trials:
- Limited Time: The trial period is often short, which may not give you enough time to fully assess the software.
- Feature Restrictions: Some free trials may have limited access to advanced features or may include ads or watermarks.
- Benefits of Free Trials:
- Money-Back Guarantee: A money-back guarantee offers peace of mind by assuring that if you are not satisfied with the product, you can receive a full refund within a specified period, typically 30 to 60 days after purchase. This removes the risk of committing to a product that may not meet your expectations.
- Benefits of Money-Back Guarantee:
- Risk-Free Investment: If the software doesn’t work as expected or meet your needs, you can easily get your money back.
- Confidence in Quality: A company that offers a money-back guarantee is often confident in the quality of their product, which is reassuring to users.
- Extended Evaluation: With the guarantee, you have more time to test the product’s full capabilities before making a final decision.
- Conditions of Money-Back Guarantee:
- Time Limits: The refund window is typically time-bound (e.g., 30 or 60 days), so you must request a refund within that period.
- Usage Restrictions: Some products may have specific conditions, such as a limit on the number of devices you can use the software on during the refund period.
- Benefits of Money-Back Guarantee:
Why Free Trials and Money-Back Guarantee Matter
Free trials and money-back guarantees are essential because they provide users with confidence that they can test the product without financial risk. Free trials allow you to ensure that the software works as advertised and meets your specific needs, while a money-back guarantee offers an extra layer of protection if the product doesn’t live up to your expectations.
These features help build trust between the company and the user. Knowing you can try the product for free or get a refund if it doesn’t work creates a sense of security, making it easier to make a purchase decision. Additionally, the ability to evaluate the product thoroughly before committing is a great way to ensure that you’re getting good value for your investment.
Advanced Features (Cloud-Based Protection, AI, etc.)
Advanced features like cloud-based protection and AI (artificial intelligence) are revolutionizing the way security software protects devices and data. These features enhance the effectiveness and efficiency of security solutions by incorporating the latest technologies to stay ahead of evolving threats. By leveraging cloud-based protection, AI algorithms, and other innovative tools, security software can provide faster, smarter, and more comprehensive protection.
Key Advanced Features
- Cloud-Based Protection:Cloud-based protection involves storing threat data and security definitions in the cloud rather than relying solely on local device databases. This allows security software to access real-time updates and global threat intelligence, which helps it detect new and emerging threats more quickly and accurately.
- Benefits of Cloud-Based Protection:
- Real-Time Updates: Cloud systems are constantly updated with the latest malware signatures and threat intelligence, offering up-to-the-minute protection against the newest threats.
- Lightweight on System Resources: Since much of the data is processed in the cloud, the software uses fewer system resources, resulting in a smoother performance on your device.
- Global Threat Intelligence: Cloud-based protection collects and analyzes threat data from millions of users worldwide, helping to identify patterns and block threats faster.
- Benefits of Cloud-Based Protection:
- AI (Artificial Intelligence):AI-powered security features utilize machine learning algorithms to detect, analyze, and respond to threats in real time. Unlike traditional security systems that rely on predefined signatures, AI security solutions can recognize abnormal patterns and behaviors that may indicate potential threats, even before they are officially recognized.
- Benefits of AI in Security:
- Proactive Threat Detection: AI uses advanced algorithms to detect new, unknown threats (zero-day threats) by analyzing unusual behavior or patterns, offering proactive protection.
- Behavioral Analysis: AI can monitor system activities and behaviors of programs, identifying potential threats based on suspicious activity rather than relying solely on traditional signatures.
- Adaptive Learning: AI-powered security software can continuously improve its threat detection by learning from new data, adapting to the latest attack methods over time.
- Benefits of AI in Security:
- Ransomware Protection: Advanced security products often include AI-driven ransomware protection, which monitors your system for signs of malicious encryption processes used by ransomware. If detected, the software can isolate affected files, stop the ransomware from spreading, and restore files from backup if necessary.
- Firewall with AI: AI-enhanced firewalls can dynamically adjust their rules and response strategies based on the current threat landscape. Instead of following fixed, predefined rules, the firewall can respond to threats in real time, blocking suspicious traffic and ensuring that only safe data is allowed to pass through.
- Automated Threat Response: Some security tools use AI to not only detect threats but also automatically respond to them. This could involve blocking malicious files, quarantining suspicious activities, or even notifying the user and security team if an attack is detected.
Ransomware Protection Process
Why Advanced Features Matter
Advanced features like cloud-based protection and AI elevate the capabilities of traditional security software, allowing it to stay ahead of increasingly sophisticated threats. As cybercriminals employ more advanced tactics, AI and cloud-based systems can provide faster and more accurate detection, ensuring that your system is protected in real-time.
For instance, cloud-based protection ensures that your device always has the latest threat definitions, even if you haven’t manually updated your software. Similarly, AI enhances detection accuracy and proactively identifies new threats before they can cause harm. With these advanced technologies, security software is not only reactive but also adaptive, continuously improving its performance and response to new challenges.
The integration of AI and cloud-based protection makes security software more efficient, less resource-intensive, and better equipped to handle the latest threats, providing peace of mind for users who need reliable protection in a constantly evolving cyber landscape.
Updates and Patches
Updates and patches are essential components of security software that ensure the product remains effective against new threats and vulnerabilities. Regular updates and patches keep the software current, improve performance, fix bugs, and enhance security features. These updates play a critical role in maintaining a high level of protection, as they address potential weaknesses in the software that could be exploited by cybercriminals.
Key Aspects of Updates and Patches
- What Are Updates and Patches?
- Updates refer to new versions or improvements to the software, which can include new features, user interface changes, or performance improvements.
- Patches are smaller updates that specifically address security vulnerabilities or bugs in the software. Patches are often released urgently when a critical flaw or exploit is discovered in the system.
- Why Updates and Patches Matter:
Regular updates and patches are crucial for ensuring that the software is able to defend against the latest threats. Without them, your security software could become outdated, leaving you vulnerable to attacks that target known weaknesses. Cybercriminals frequently exploit unpatched vulnerabilities to gain unauthorized access to systems, so timely patching is a key part of any comprehensive security strategy. - Types of Updates and Patches:
- Security Patches: These patches fix critical vulnerabilities or bugs that hackers could exploit. Security patches are typically released on an as-needed basis, especially if a new vulnerability is discovered.
- Feature Updates: These updates introduce new features or enhancements to the software, improving the user experience and adding additional functionality.
- Bug Fixes and Performance Updates: These updates address minor issues, such as crashes or slow performance, ensuring that the software runs smoothly and efficiently.
- How Updates and Patches Improve Security:
When you install updates and patches, the security software is equipped with the latest protections against threats. This includes protection from new types of malware, ransomware, phishing attempts, and zero-day vulnerabilities. Without regular updates, your device could be exposed to attacks that exploit security gaps. - Automated vs. Manual Updates: Many modern security tools offer automated updates, meaning the software will automatically check for and install the latest updates and patches without user intervention. This ensures that your software stays up-to-date without you having to worry about it. However, some users prefer to manually control when and how updates are installed, especially if they want to wait for feedback from other users or ensure compatibility with other software.
- Frequency of Updates and Patches: The frequency of updates and patches varies depending on the software. Security software companies typically release critical security patches immediately after a vulnerability is discovered, while feature updates may be released on a monthly or quarterly basis. It’s important to check for updates regularly to make sure you’re protected at all times.
Why Timely Updates and Patches Are Crucial
Updates and patches are vital to the ongoing effectiveness of any security software. As new threats are discovered, attackers quickly find ways to exploit vulnerabilities in outdated software. By keeping your security software up-to-date, you significantly reduce the risk of these threats affecting your system. Without proper updates, even the best antivirus software can become ineffective over time, leaving you vulnerable to attack.
For example, if a vulnerability is discovered in the way the software scans files or processes downloads, a patch would be issued to fix that specific vulnerability. Failing to install this patch would allow malware to bypass detection and compromise your system. With regular updates, your security software can defend against these emerging threats.
Additionally, updates and patches often improve the software’s performance and stability, ensuring that it runs smoothly on your system and doesn’t interfere with other programs. Software updates also ensure compatibility with newer operating systems, preventing any issues that may arise from outdated versions.

